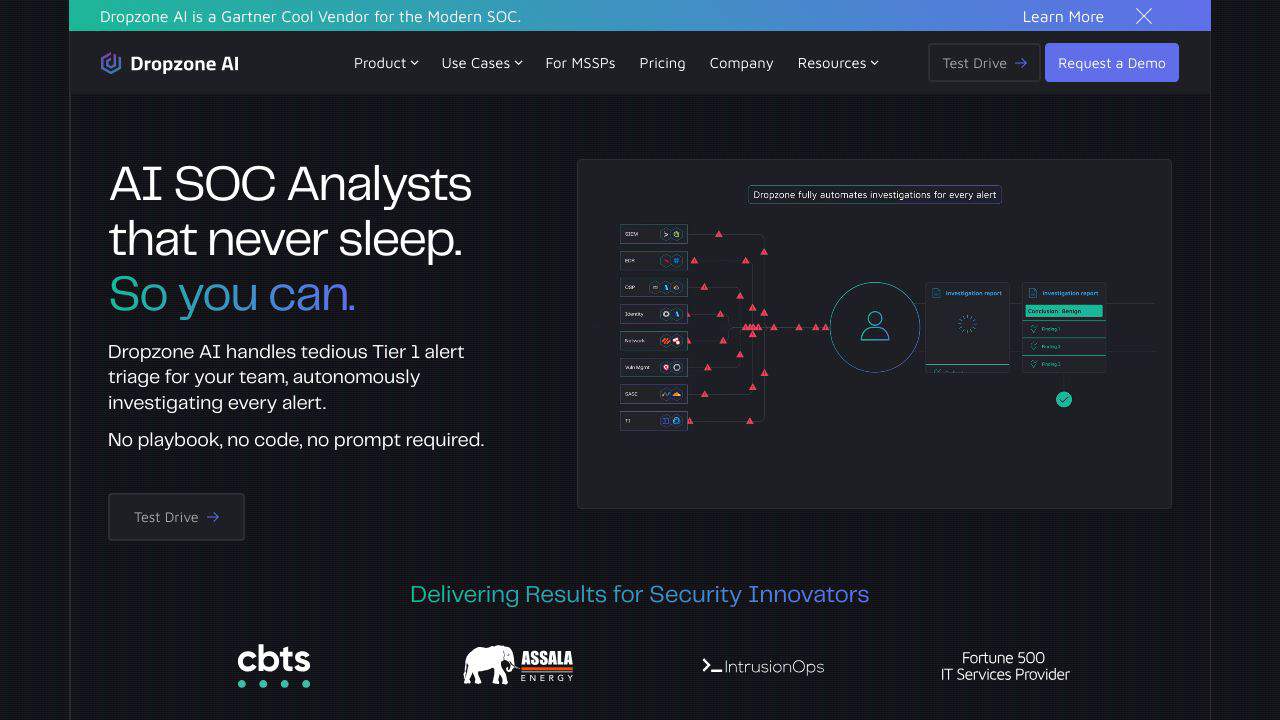
What is Dropzone?
Dropzone is an advanced AI tool designed to enhance the efficiency of Security Operations Centers (SOCs) by automating the investigation of security alerts. This innovative tool operates autonomously, allowing cybersecurity teams to focus on more complex tasks. With its ability to handle alerts without the need for playbooks or prompts, Dropzone is a game-changer in the fight against cybersecurity threats.
Dropzone Features
- Autonomous Alert Investigations: Manages various types of security alerts, such as phishing and network breaches, independently.
- Integration with Existing Tools: Supports over 50 integrations, including major platforms like Cisco Secure Firewall and Microsoft Office365.
- Pre-trained AI Agents: Equipped with operational AI agents from day one, eliminating the need for custom playbook development.
- Evidence-Based Reporting: Provides detailed evidence with each investigation, ensuring transparency and reliability.
Dropzone Use Cases
Dropzone can be utilized in various scenarios, making it a versatile tool for different users:
- Corporate Security Teams: Efficiently manage high volumes of security alerts.
- Managed Security Service Providers (MSSPs): Enhance service offerings by integrating Dropzone into their operations.
- Financial Institutions: Protect sensitive data and meet regulatory requirements through automated investigations.
- Healthcare Providers: Safeguard patient data by quickly identifying and addressing potential threats.
- Non-profits: Protect donor information effectively.
- Educational Institutions: Prevent data breaches cost-effectively.
Conclusion
In summary, Dropzone stands out as a powerful tool for modern cybersecurity operations. By autonomously handling security alerts and integrating seamlessly with existing systems, it significantly reduces response times and allows teams to focus on real threats. With its robust AI technology and user-centric features, Dropzone not only optimizes security processes but also empowers teams to tackle more strategic challenges in the ever-evolving landscape of cybersecurity.